Virtual Private Network (VPN) is a method to connect between nodes network by utilizing the Internet connection (public network/WAN) and using encrypted protocols making it more secure. A VPN is one surefire solution for connecting multiple locations are far apart to easily use the Internet connections of each place.
An example of its application is when you are managing networks for several offices in different locations and far from each other. To connect the Office using the link all physical will certainly must a large fee. Well, by using VPN we could set up a link between the offices by leveraging existing internet network. The links are formed equipped with encryption to decrease the possibility of data will be accessed by people who are not responsible.
VPN on Mikrotik support several methods, such as PPTP, SSTP, L2TP, and OpenVPN. With the presence of some of these options, we need to choose the type of VPN network that suits us. In general all type has the same function. The difference is authentication and encryption used.
At this time the Mikrotik Tutorial we discuss one type and the type of VPN in Mikrtotik:
PPTP (Point to Point Tunnel Protocol)
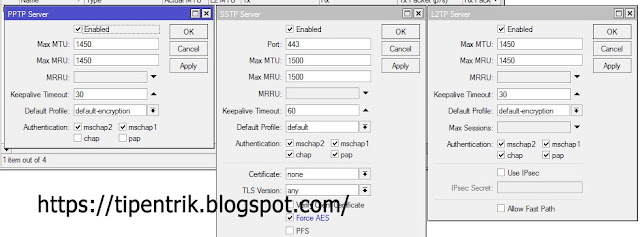
PPTP VPN type is one of the simplest in the configuration. In addition it is also flexible. The majority of the operating system already support as a PPTP Client, either on a PC or operating system gadget android. Communication using PPTP protocol TCP port 1723, and using IP Protocol 47/GRE encapsulation for packet data. On the setting of PPTP, we can define a network security protocol that is used for authentication process PPTP at Arabian Ranches, such as the pap, chap, mschap and mschap2. Then after the tunnel is formed, the transmitted data is encrypted using Microsoft Point to Point Encryption (MPPE). The process of enskripsi will usually make the transmitted packet header size will increase. If we are monitoring, traffic passing through PPTP tunnel will have 7% overhead.
L2TP (Layer 2 Tunnel Protocol)
L2TP is a development of PPTP plus L2F. Network security and Encryption Protocol used to authenticate the same by PPTP. But to do the communication, L2TP uses UDP port 1701. Usually for a better security, L2TP is combined with IPSec, L2TP/IPSec into. For example for a Windows Operating system, by default Windows OS using L2TP/IPSec. However, the consequences of course configuration to do not se-simple PPTP. Any client side should support IPSec when implementing L2TP/IPSec. In terms of encryption, the encryption on L2TP/IPSec have levels higher than the securities using PPTP MPPE. Traffic through the tunnel L2TP will experience 12% overhead.
SSTP (Secure Socket Tunneling Protocol)
To build a VPN SSTP method required SSL certificate on each device, except that both use the RouterOS. SSTP communication using TCP port 443 (SSL), the same thing its like a secure website (https). You should make sure the clock is in compliance with the real-time if using the certificate. Manyamakan time routers with real-time Client NTP feature can. Unfortunately not all OS Support SSTP VPN methods. Traffic through the tunnel SSTP will experience 12% overhead.
OpenVPN
A VPN is used when data security required reply. By default, uses UDP OpenVPN port 1194 and the required certificate on each device to be connected. For client compatibility, OpenVPN can be built almost on all Operating systems with the help of third-party applications. OpenVPN uses algorithm sha1 and md5 for authentication process, and using multiple ciphers namely blowfish128, aes128, aes192 and aes256. Traffic through OpenVPN tunnel will have 16% overhead.
Conclusion
Keep in mind, the more you want a secure network, it will be increasingly complex configuration that needs to be applied. Similarly, with the use of a hardware resource, the higher the encryption used, resource usage, especially the cpu will also rise.
So in conclusion, if you want a VPN with compatibility and support tools client Jim-dandy, then PPTP can be so choice. In addition to his high kompatbilitas, PPTP VPN is also easier in the configuration of Mikrotik. But if you want a VPN with a better level of security, then L2TP/IPSec or OpenVPN is his solution.
On most Windows OS by default, L2TP/IPSec, wear so live diseusuaikan on the server-side. If your tool support and security you want high on line your VPN, L2TP/IPSec can so the right choice
Comments